This ITIL report evaluates technologies and applications in terms of their business impact, adoption rate and maturity level to help users decide where and when to invest.
The Predictive Analytics Scores below – ordered on Forecasted Future Needs and Demand from High to Low – shows you ITIL’s Predictive Analysis. The link takes you to a corresponding product in The Art of Service’s store to get started.
The Art of Service’s predictive model results enable businesses to discover and apply the most profitable technologies and applications, attracting the most profitable customers, and therefore helping maximize value from their investments. The Predictive Analytics algorithm evaluates and scores technologies and applications.
The platform monitors over six thousand technologies and applications for months, looking for interest swings in a topic, concept, technology or application, not just a count of mentions. It then makes forecasts about the velocity of the interest over time, with peaks representing it breaking into the mainstream. Data sources include trend data, employment data, employee skills data, and signals like advertising spent, advertisers, search-counts, youtube activity, patents, and books published.
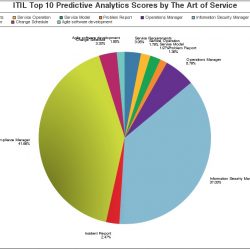
Predictive Analytics Scores:
017721 – Compliance Manager
015754 – Information Security Manager
002461 – Operations Manager
001418 – Change Schedule
001298 – Service Requirements
001051 – Incident Report
000838 – Service Model
000761 – Service Operation
000659 – Agile software development
000580 – Problem Report
000558 – Problem Identification
000506 – Service Assessment
000472 – Service Request
000429 – Security Incident
000376 – Access and Identity Management
000372 – Change Proposal
000368 – Customer Complaint
000363 – Support Request
000357 – Service Desk
000355 – Release Planning
000351 – Incident Resolution
000348 – Service Support
000340 – Request for Service
000340 – Compliance Review
000306 – Availability Test
000298 – Call center
000276 – Request Fulfillment
000263 – Change Record
000256 – Process Area
000254 – Configuration Item
000250 – Service Definition
000248 – Fishbone diagram
000243 – Best practice
000235 – Access Management
000229 – Release Build
000228 – 5 Whys
000226 – Service Review
000209 – Security Review
000207 – ITSM
000199 – Release Deployment
000196 – Customer Portfolio
000190 – Change request
000189 – Service Delivery
000182 – Release Policy
000176 – Emergency Change
000170 – Service level
000168 – Availability Report
000167 – Project Charter
000164 – Release Unit
000159 – Release Management
000158 – Status Inquiry
000158 – Service catalog
000153 – Request for Change
000152 – Continual Service Improvement
000150 – Release Plan
000150 – Capacity Report
000144 – Capacity Plan
000142 – SKMS
000132 – Functional Management
000127 – Service Management System
000126 – Service Owner
000123 – Service Portfolio
000123 – Configuration Manager
000122 – Application Framework
000119 – Application Development
000117 – Budget Request
000113 – Compliance Management
000113 – Availability Plan
000111 – CMDB
000109 – Incident Closure
000108 – Standard Terms and Conditions
000108 – Risk Monitoring
000104 – Change Owner
000103 – Risk Management Policy
000102 – Acceptance Test
000100 – Incident Management
000099 – Identity management
000097 – Emergency Plan
000096 – Process Owner
000096 – Availability Management
000095 – Purchase Request
000094 – Event Review
000090 – Help desk
000088 – ISO/IEC 27001
000086 – Capacity Management
000086 – Application Management
000084 – Problem Management
000080 – Definitive Media Library
000079 – Change Management Policy
000077 – Configuration Audit
000076 – Process Evaluation
000074 – Incident Manager
000073 – Risk Register
000072 – Business case
000070 – Service Transition
000069 – Corrective and preventive action
000068 – RACI matrix
000066 – Service Charter
000066 – Problem Priority
000064 – Demand Management
000063 – Technical Analyst
000061 – Supplier Management
000060 – Service Design
000059 – Technical Management
000059 – Process Design
000059 – Process Architecture
000058 – ECAB
000057 – Application Manager
000057 – Application Developer
000056 – Test Model
000056 – Service Strategy
000054 – Test Manager
000054 – Process Audit
000054 – Business Relationship Manager
000053 – Supplier Manager
000053 – Service Catalogue
000051 – Change Evaluation
000050 – Risk Manager
000049 – Service Design Package
000049 – Incident Record
000047 – Service Portfolio Management
000047 – Facilities Management
000046 – Risk Management
000046 – Business impact analysis
000041 – Strategic Action Plan
000041 – COBIT
000039 – SLA Review
000039 – IT Operations Management
000037 – Process Architect
000030 – Demand Manager
000030 – Capacity Manager
000029 – IT Operations Manager
000028 – Security Management Information System
000028 – Knowledge Manager
000024 – Change Manager
000023 – Project Coordination
000023 – PDCA
000023 – Ishikawa diagram
000022 – Change Management
000020 – Program management
000018 – ISACA
000016 – Business Service Management
000015 – TM Forum
000015 – Lean manufacturing
000015 – IT Operator
000015 – Change Classification
000015 – Business Relationship Management
000015 – Availability Manager
000010 – Project Control
000008 – ISO/IEC 27002
000007 – Service Level Manager
000006 – Information and Communication Technology
000006 – Compliance Register
000005 – IT Service Management
000003 – PRINCE2
000000 – Axelos
Evaluation Criteria Definitions:
Interest and Popularity:
Leaders:
100 – Service Desk
100 – Emergency Change
100 – Continual Service Improvement
Google Trends data for gauging mindshare and awareness, the numbers are relative to their maximum (100), meaning number 100 has maximum interest right now and number 50 has half the interest it had from its peak of 100.
Employment Demand:
Leaders:
519511 – Operations Manager
252331 – Compliance Manager
106634 – Information Security Manager
Open employment opportunities on the date of this report for the subject. Indicator of the need of employers for this specific skill set and therefore their organization’s application of it in relation to the other subjects.
Active Practitioners:
Leaders:
06738366 – Change Management
05674323 – Program management
04466125 – Risk Management
Number of practitioners and professionals which have the subject skill set and experience. Indicator of the need of employers (and availability of employees) for this specific skill set and therefore their organization’s application of it in relation to the other subjects.
Monthly Searches:
Leaders:
110000 – PDCA
110000 – Call center
090500 – Risk Management
How often a month a search is performed for the keyword/phrase: and indicator of interest in the subject.
Cost per Click:
Leaders:
016.33 – Application Development
015.96 – Facilities Management
015.92 – IT Service Management
CPC: The average amount advertisers pay Google anytime someone clicks their own ad for this keyword. Indicator of the advertising being spent on the topic ergo investments being made to attract clients.
Active Advertisers:
Leaders:
082 – Application Development
082 – Application Developer
065 – IT Service Management
This shows how many unique advertisers have appeared on this subject in the last 12 months. Indicator of the advertising being spent on the topic ergo investments being made to attract clients.
Patents:
Leaders:
00078000 – Service Request
00062400 – Service level
00059000 – Request for Service
Patents issued for the specific subject. Indicator of R&D investments and innovation in the specific subject.
Books in print:
Leaders:
00084800 – Best practice
00058031 – IT Operator
00046200 – Risk Management
Number of in-print books that cover the subject. Indicator of the need for knowledge sharing and its availability.
Youtube content:
Leaders:
02320000 – Risk Management
00389000 – Call center
00169000 – Best practice
Number of youtube content videos that cover the subject. Indicator of the need for knowledge sharing and its availability.
Complete Overview:
Interest and Popularity
100 – Service Desk
100 – Emergency Change
100 – Continual Service Improvement
100 – Access and Identity Management
099 – Call center
098 – Support Request
098 – Service Request
098 – Change request
098 – Axelos
097 – Request for Change
097 – PDCA
096 – Request for Service
096 – Incident Report
096 – Customer Complaint
093 – RACI matrix
092 – Operations Manager
088 – Change Record
087 – Incident Manager
087 – Compliance Manager
084 – Service Delivery
084 – 5 Whys
083 – IT Operator
082 – Service Transition
082 – Release Build
082 – Fishbone diagram
081 – Application Manager
080 – Service Definition
080 – ITSM
079 – Service Support
079 – Availability Test
078 – SKMS
078 – Change Manager
077 – Technical Analyst
076 – Change Schedule
075 – Test Model
075 – Service Requirements
074 – Test Manager
074 – Service Owner
074 – Demand Manager
073 – Service Charter
073 – Release Planning
072 – Incident Closure
071 – Supplier Manager
070 – Problem Report
069 – Release Unit
069 – Capacity Plan
068 – ISO/IEC 27001
067 – Release Deployment
067 – Business Relationship Manager
066 – Change Classification
066 – Agile software development
065 – Status Inquiry
065 – Risk Monitoring
065 – Best practice
064 – Incident Management
063 – Service Model
063 – Process Area
062 – Service Operation
062 – Purchase Request
062 – Process Owner
062 – Capacity Report
061 – Configuration Manager
060 – Change Proposal
057 – Service Review
057 – Service Catalogue
057 – Release Policy
057 – Release Management
057 – Compliance Management
057 – Capacity Manager
056 – IT Operations Manager
055 – Project Charter
055 – Change Owner
054 – Service Portfolio
054 – Service Assessment
054 – Security Incident
054 – Risk Manager
053 – Process Audit
053 – Information and Communication Technology
053 – ECAB
053 – Customer Portfolio
052 – IT Operations Management
052 – Compliance Review
052 – Acceptance Test
051 – Access Management
050 – Request Fulfillment
050 – Ishikawa diagram
050 – Incident Resolution
050 – CMDB
050 – Availability Manager
049 – Application Management
048 – Risk Register
047 – Service Design
047 – Availability Management
046 – Service Level Manager
046 – Configuration Item
045 – Service Management System
045 – Process Evaluation
045 – PRINCE2
045 – ISACA
045 – Functional Management
045 – Compliance Register
044 – Security Review
044 – Help desk
044 – Application Framework
043 – Process Design
043 – ISO/IEC 27002
043 – Demand Management
042 – Service catalog
042 – Facilities Management
042 – Business Relationship Management
041 – Release Plan
041 – Project Coordination
041 – Change Management
040 – Supplier Management
040 – Service Strategy
040 – Service Portfolio Management
040 – Service level
040 – Information Security Manager
040 – Availability Plan
039 – SLA Review
039 – Project Control
039 – Identity management
038 – Risk Management Policy
038 – IT Service Management
038 – Incident Record
037 – Technical Management
037 – Knowledge Manager
037 – Change Evaluation
037 – Availability Report
036 – TM Forum
036 – Strategic Action Plan
036 – Program management
036 – Problem Identification
036 – Lean manufacturing
036 – Business impact analysis
036 – Application Development
035 – Process Architecture
035 – Process Architect
035 – Definitive Media Library
035 – Change Management Policy
034 – Service Design Package
034 – Risk Management
034 – Capacity Management
034 – Application Developer
033 – Security Management Information System
033 – Problem Management
033 – Budget Request
032 – Event Review
032 – Configuration Audit
032 – Business Service Management
032 – Business case
031 – Standard Terms and Conditions
031 – Problem Priority
031 – Emergency Plan
031 – Corrective and preventive action
031 – COBIT
Employment Demand:
519511 – Operations Manager
252331 – Compliance Manager
106634 – Information Security Manager
060571 – Risk Management
035658 – Change Management
034618 – Call center
030842 – Program management
030238 – Service Delivery
029893 – Application Development
020666 – Best practice
017096 – Service level
015527 – Help desk
013719 – Service Support
013546 – Service Desk
009211 – Lean manufacturing
007755 – Business case
007355 – Service Requirements
007241 – Facilities Management
007003 – Service Operation
005807 – Agile software development
005540 – Incident Management
005369 – Process Design
005345 – Service Model
005316 – Application Developer
004976 – Release Management
004507 – Problem Identification
004378 – Project Coordination
004147 – Problem Management
004084 – Access Management
002846 – Service Request
002821 – Identity management
002610 – Technical Management
002529 – ITSM
002463 – Supplier Management
002461 – Customer Complaint
002179 – Security Incident
002122 – Compliance Management
002063 – Compliance Review
002034 – COBIT
001876 – Acceptance Test
001811 – IT Service Management
001737 – Incident Report
001639 – Application Management
001611 – Risk Manager
001590 – Change request
001578 – Customer Portfolio
001570 – Capacity Management
001527 – Service Design
001516 – Configuration Manager
001235 – Technical Analyst
001211 – Incident Resolution
001184 – Release Planning
001137 – Project Control
001061 – Functional Management
001019 – Demand Management
000921 – Process Owner
000845 – Project Charter
000829 – CMDB
000800 – Test Manager
000773 – Service Strategy
000771 – Application Framework
000765 – Service Review
000596 – Service catalog
000573 – Service Portfolio
000540 – Process Area
000517 – PDCA
000506 – Corrective and preventive action
000466 – Security Review
000394 – ISACA
000390 – Process Evaluation
000387 – Application Manager
000377 – Change Schedule
000369 – Emergency Plan
000338 – Risk Monitoring
000330 – Release Deployment
000329 – Request Fulfillment
000323 – Process Audit
000317 – Problem Report
000317 – PRINCE2
000315 – Business Relationship Management
000314 – Service Assessment
000308 – Continual Service Improvement
000304 – Risk Register
000293 – Service Transition
000283 – Change Manager
000257 – Incident Manager
000248 – Release Plan
000244 – Business Relationship Manager
000242 – Business impact analysis
000237 – Request for Service
000235 – Support Request
000229 – Availability Management
000221 – Service Management System
000220 – Purchase Request
000205 – Risk Management Policy
000200 – Process Architecture
000200 – Capacity Plan
000195 – Change Proposal
000191 – Service Owner
000183 – ISO/IEC 27001
000178 – IT Operations Management
000161 – Budget Request
000156 – Service Definition
000156 – Knowledge Manager
000153 – 5 Whys
000150 – Request for Change
000136 – Availability Report
000114 – IT Operations Manager
000106 – Configuration Item
000105 – Information and Communication Technology
000099 – Service Catalogue
000090 – Process Architect
000089 – Standard Terms and Conditions
000087 – Release Build
000077 – Supplier Manager
000073 – Demand Manager
000073 – Change Management Policy
000072 – Event Review
000069 – Fishbone diagram
000067 – Access and Identity Management
000058 – Business Service Management
000046 – Configuration Audit
000043 – Change Record
000039 – Strategic Action Plan
000039 – Availability Test
000038 – Service Portfolio Management
000036 – Capacity Report
000033 – Capacity Manager
000031 – Emergency Change
000030 – Availability Plan
000028 – Test Model
000024 – Change Owner
000020 – Release Policy
000019 – Service Charter
000019 – ECAB
000018 – TM Forum
000018 – Change Evaluation
000017 – RACI matrix
000016 – Status Inquiry
000016 – Incident Closure
000015 – SLA Review
000014 – Incident Record
000013 – Release Unit
000011 – Service Level Manager
000011 – ISO/IEC 27002
000011 – Availability Manager
000010 – Ishikawa diagram
000008 – IT Operator
000007 – SKMS
000004 – Problem Priority
000004 – Definitive Media Library
000003 – Service Design Package
000001 – Compliance Register
000000 – Security Management Information System
000000 – Change Classification
000000 – Axelos
Active Practitioners:
06738366 – Change Management
05674323 – Program management
04466125 – Risk Management
02211492 – Lean manufacturing
01941912 – Operations Manager
01343196 – Service Delivery
01296626 – IT Service Management
01149298 – Call center
00907908 – Application Development
00775707 – Project Coordination
00759513 – Help desk
00646382 – Facilities Management
00552235 – Best practice
00448125 – PRINCE2
00444174 – Project Control
00402284 – Service level
00393086 – Process Design
00379080 – Service Desk
00353257 – Incident Management
00344031 – Business case
00317741 – Application Developer
00311010 – Service Support
00218962 – PDCA
00178709 – Release Management
00174739 – Risk Manager
00163724 – Technical Management
00163233 – Problem Management
00162022 – Supplier Management
00155462 – COBIT
00150825 – Technical Analyst
00123879 – Compliance Manager
00120147 – Service Design
00111018 – Identity management
00109210 – Test Manager
00107094 – Compliance Management
00097659 – ITSM
00097442 – ISACA
00095503 – Acceptance Test
00093490 – Change Manager
00093337 – Application Management
00088703 – Access Management
00086287 – Information and Communication Technology
00085960 – Business Relationship Management
00082092 – Change request
00075093 – Configuration Manager
00070713 – Axelos
00068119 – Demand Management
00064184 – Customer Complaint
00061973 – Capacity Management
00059547 – Process Owner
00059054 – Service Request
00058165 – Agile software development
00057092 – Service Operation
00055279 – Service Strategy
00054674 – Application Manager
00042565 – Customer Portfolio
00042489 – Service Requirements
00040190 – Service Model
00037502 – CMDB
00036186 – Functional Management
00034320 – Service Transition
00031546 – Compliance Review
00031543 – Process Audit
00030204 – Business Relationship Manager
00030132 – Incident Manager
00029090 – Problem Identification
00027777 – Project Charter
00027722 – Application Framework
00027443 – Security Incident
00027074 – Information Security Manager
00025239 – Service Portfolio
00024331 – Release Planning
00023676 – IT Operations Management
00022955 – Process Evaluation
00022863 – Corrective and preventive action
00022356 – IT Operations Manager
00020856 – Knowledge Manager
00020313 – Risk Monitoring
00020277 – Continual Service Improvement
00020034 – Risk Register
00019293 – Service Review
00019027 – Business impact analysis
00018209 – Demand Manager
00017263 – Incident Resolution
00015865 – Incident Report
00015846 – Service catalog
00014353 – Purchase Request
00014213 – ISO/IEC 27001
00013299 – Process Area
00011846 – Emergency Plan
00011832 – Process Architecture
00011695 – Business Service Management
00011212 – Availability Management
00011206 – Service Owner
00011128 – Release Deployment
00010706 – Service Catalogue
00010413 – Supplier Manager
00009806 – Security Review
00009581 – Capacity Plan
00009504 – Request for Change
00008507 – Process Architect
00007842 – Service Management System
00007548 – Risk Management Policy
00007470 – Service Level Manager
00006779 – Release Plan
00006691 – Request for Service
00006337 – Support Request
00006260 – Capacity Manager
00005957 – Request Fulfillment
00005642 – 5 Whys
00005567 – ISO/IEC 27002
00005002 – Service Definition
00004525 – Budget Request
00004432 – TM Forum
00004350 – IT Operator
00003824 – Problem Report
00003765 – Test Model
00003637 – Availability Manager
00003466 – Strategic Action Plan
00003352 – Service Assessment
00003244 – Change Management Policy
00003222 – Service Portfolio Management
00003145 – Change Proposal
00003112 – Release Build
00003002 – Availability Report
00002551 – Standard Terms and Conditions
00002453 – Event Review
00002316 – RACI matrix
00002282 – Fishbone diagram
00002144 – Ishikawa diagram
00002114 – Service Charter
00002021 – Change Schedule
00001922 – Configuration Item
00001912 – Configuration Audit
00001781 – Access and Identity Management
00001762 – Emergency Change
00001744 – ECAB
00001500 – SLA Review
00001488 – Capacity Report
00001441 – Change Record
00001295 – Change Evaluation
00001269 – Change Owner
00001080 – Incident Record
00001063 – Availability Plan
00001058 – Incident Closure
00001008 – Availability Test
00000694 – Compliance Register
00000658 – Status Inquiry
00000626 – Release Policy
00000548 – Release Unit
00000439 – Change Classification
00000384 – SKMS
00000207 – Service Design Package
00000188 – Problem Priority
00000176 – Definitive Media Library
00000120 – Security Management Information System
Monthly Searches:
110000 – PDCA
110000 – Call center
090500 – Risk Management
074000 – Lean manufacturing
074000 – Change Management
049500 – PRINCE2
040500 – ISACA
040500 – Help desk
040500 – COBIT
040500 – Best practice
033100 – ITSM
033100 – Fishbone diagram
027100 – Business case
022200 – Project Charter
022200 – Facilities Management
022200 – CMDB
018100 – Service Desk
018100 – Operations Manager
014800 – Incident Report
012100 – Agile software development
009900 – Ishikawa diagram
009900 – Incident Management
008100 – Program management
008100 – Information and Communication Technology
008100 – Application Manager
006600 – Service Definition
006600 – Risk Register
006600 – Release Management
006600 – Identity management
006600 – ECAB
006600 – 5 Whys
005400 – Application Development
004410 – Service Delivery
004410 – Risk Manager
004410 – IT Service Management
004410 – Demand Management
003600 – TM Forum
003600 – Process Design
003600 – Problem Management
003600 – Compliance Management
003600 – Change request
003600 – Capacity Management
003600 – Business impact analysis
002910 – Test Manager
002910 – Service level
002910 – Configuration Manager
002910 – Compliance Manager
002910 – Application Management
002910 – Access Management
002400 – Supplier Management
002400 – Service catalog
001890 – Technical Analyst
001890 – Service Request
001890 – Risk Management Policy
001890 – Project Control
001890 – Process Evaluation
001890 – Emergency Plan
001890 – Change Manager
001890 – Application Developer
001890 – Acceptance Test
001590 – Service Catalogue
001590 – Customer Complaint
001290 – Service Strategy
001290 – Process Owner
000990 – Problem Identification
000990 – Configuration Item
000990 – Business Relationship Management
000870 – Technical Management
000870 – Service Support
000870 – Service Model
000870 – Request for Change
000870 – Process Audit
000870 – Knowledge Manager
000870 – Corrective and preventive action
000870 – Business Service Management
000870 – Availability Management
000870 – Application Framework
000720 – Service Portfolio Management
000720 – IT Operations Manager
000720 – Demand Manager
000600 – Service Operation
000600 – Security Incident
000600 – Release Planning
000600 – Process Architecture
000600 – Compliance Review
000600 – Change Owner
000600 – Capacity Plan
000480 – Standard Terms and Conditions
000480 – Service Management System
000480 – Risk Monitoring
000480 – Request Fulfillment
000480 – IT Operations Management
000480 – Change Management Policy
000390 – Information Security Manager
000330 – Strategic Action Plan
000270 – Service Review
000270 – Security Review
000270 – Compliance Register
000210 – Supplier Manager
000210 – Capacity Manager
000180 – Configuration Audit
000090 – Incident Resolution
000000 – Test Model
000000 – Support Request
000000 – Status Inquiry
000000 – SLA Review
000000 – SKMS
000000 – Service Transition
000000 – Service Requirements
000000 – Service Portfolio
000000 – Service Owner
000000 – Service Level Manager
000000 – Service Design Package
000000 – Service Design
000000 – Service Charter
000000 – Service Assessment
000000 – Security Management Information System
000000 – Request for Service
000000 – Release Unit
000000 – Release Policy
000000 – Release Plan
000000 – Release Deployment
000000 – Release Build
000000 – RACI matrix
000000 – Purchase Request
000000 – Project Coordination
000000 – Process Area
000000 – Process Architect
000000 – Problem Report
000000 – Problem Priority
000000 – IT Operator
000000 – ISO/IEC 27002
000000 – ISO/IEC 27001
000000 – Incident Record
000000 – Incident Manager
000000 – Incident Closure
000000 – Functional Management
000000 – Event Review
000000 – Emergency Change
000000 – Definitive Media Library
000000 – Customer Portfolio
000000 – Continual Service Improvement
000000 – Change Schedule
000000 – Change Record
000000 – Change Proposal
000000 – Change Evaluation
000000 – Change Classification
000000 – Capacity Report
000000 – Business Relationship Manager
000000 – Budget Request
000000 – Axelos
000000 – Availability Test
000000 – Availability Report
000000 – Availability Plan
000000 – Availability Manager
000000 – Access and Identity Management
Cost per Click:
016.33 – Application Development
015.96 – Facilities Management
015.92 – IT Service Management
013.75 – IT Operations Management
013.64 – Incident Management
013.35 – Business Service Management
012.78 – Application Developer
012.34 – IT Operations Manager
011.36 – Agile software development
010.47 – Identity management
009.93 – Capacity Management
009.59 – Configuration Manager
009.52 – Help desk
009.45 – Security Incident
009.27 – Change Management Policy
009.23 – Service Portfolio Management
009.19 – CMDB
009.14 – Request Fulfillment
008.63 – Configuration Audit
008.58 – Supplier Manager
008.53 – Demand Manager
008.07 – Service Desk
008.04 – Configuration Item
007.93 – Access Management
007.65 – Technical Management
007.54 – Call center
007.42 – Corrective and preventive action
007.14 – ITSM
007.12 – Supplier Management
006.99 – Demand Management
006.91 – Application Manager
006.81 – Service Catalogue
006.52 – Service Definition
006.26 – Security Review
005.93 – Lean manufacturing
005.79 – Capacity Plan
005.76 – Application Management
005.47 – Compliance Management
005.29 – Incident Resolution
005.24 – Process Architecture
005.16 – Strategic Action Plan
005.12 – Risk Manager
005.06 – Risk Management
004.62 – Process Evaluation
004.58 – Release Management
004.58 – Program management
004.38 – Service level
004.28 – Change Management
003.95 – Change Manager
003.92 – Service catalog
003.90 – Technical Analyst
003.67 – Change Owner
003.63 – TM Forum
003.40 – Service Delivery
003.33 – Compliance Manager
003.02 – Business case
002.82 – PRINCE2
002.81 – Process Owner
002.70 – Service Model
002.30 – Request for Change
002.15 – Process Design
002.11 – Capacity Manager
002.09 – Test Manager
002.07 – Problem Management
001.86 – Service Strategy
001.84 – Service Request
001.64 – Emergency Plan
001.59 – Risk Management Policy
001.53 – Standard Terms and Conditions
001.41 – Release Planning
001.23 – Risk Register
001.11 – Customer Complaint
001.09 – Compliance Review
001.03 – Service Management System
000.94 – Project Control
000.86 – Service Review
000.83 – Information Security Manager
000.70 – Business impact analysis
000.64 – Risk Monitoring
000.57 – Process Audit
000.55 – Knowledge Manager
000.52 – Incident Report
000.50 – Availability Management
000.49 – Application Framework
000.42 – Problem Identification
000.34 – Project Charter
000.22 – Compliance Register
000.20 – Change request
000.19 – Acceptance Test
000.17 – Business Relationship Management
000.10 – Operations Manager
000.09 – Ishikawa diagram
000.06 – Information and Communication Technology
000.05 – PDCA
000.05 – ISACA
000.05 – 5 Whys
000.04 – Service Support
000.04 – Fishbone diagram
000.04 – Best practice
000.03 – ECAB
000.03 – COBIT
000.02 – Service Operation
000.00 – Test Model
000.00 – Support Request
000.00 – Status Inquiry
000.00 – SLA Review
000.00 – SKMS
000.00 – Service Transition
000.00 – Service Requirements
000.00 – Service Portfolio
000.00 – Service Owner
000.00 – Service Level Manager
000.00 – Service Design Package
000.00 – Service Design
000.00 – Service Charter
000.00 – Service Assessment
000.00 – Security Management Information System
000.00 – Request for Service
000.00 – Release Unit
000.00 – Release Policy
000.00 – Release Plan
000.00 – Release Deployment
000.00 – Release Build
000.00 – RACI matrix
000.00 – Purchase Request
000.00 – Project Coordination
000.00 – Process Area
000.00 – Process Architect
000.00 – Problem Report
000.00 – Problem Priority
000.00 – IT Operator
000.00 – ISO/IEC 27002
000.00 – ISO/IEC 27001
000.00 – Incident Record
000.00 – Incident Manager
000.00 – Incident Closure
000.00 – Functional Management
000.00 – Event Review
000.00 – Emergency Change
000.00 – Definitive Media Library
000.00 – Customer Portfolio
000.00 – Continual Service Improvement
000.00 – Change Schedule
000.00 – Change Record
000.00 – Change Proposal
000.00 – Change Evaluation
000.00 – Change Classification
000.00 – Capacity Report
000.00 – Business Relationship Manager
000.00 – Budget Request
000.00 – Axelos
000.00 – Availability Test
000.00 – Availability Report
000.00 – Availability Plan
000.00 – Availability Manager
000.00 – Access and Identity Management
Active Advertisers
082 – Application Development
082 – Application Developer
065 – IT Service Management
058 – Service Management System
057 – Risk Management
056 – Help desk
050 – Program management
050 – Identity management
047 – Business Service Management
044 – Compliance Management
044 – Call center
042 – Supplier Management
042 – Service Portfolio Management
041 – Service Desk
037 – Service Support
036 – IT Operations Management
036 – Application Management
034 – Agile software development
033 – Incident Management
033 – Access Management
032 – Lean manufacturing
030 – Change Management
029 – Facilities Management
027 – Emergency Plan
026 – ITSM
025 – Service catalog
018 – Corrective and preventive action
018 – Capacity Plan
017 – Risk Management Policy
017 – Release Management
017 – Information Security Manager
016 – Service Catalogue
016 – Process Audit
016 – IT Operations Manager
016 – Business impact analysis
015 – Capacity Management
015 – Business Relationship Management
014 – Risk Monitoring
014 – Risk Manager
014 – Change Management Policy
013 – Process Design
012 – Technical Management
012 – Service Delivery
012 – Problem Management
011 – Supplier Manager
011 – Strategic Action Plan
011 – Incident Report
011 – Demand Management
011 – Customer Complaint
011 – Compliance Manager
010 – Security Incident
010 – Fishbone diagram
010 – Configuration Manager
010 – CMDB
009 – Security Review
009 – Knowledge Manager
009 – Compliance Review
009 – Availability Management
007 – Change Manager
007 – Application Manager
006 – Risk Register
006 – Application Framework
005 – Standard Terms and Conditions
004 – Service Strategy
004 – Project Charter
004 – Incident Manager
003 – Test Manager
003 – Request Fulfillment
003 – COBIT
003 – 5 Whys
002 – Service Request
002 – Service Operation
002 – Release Planning
002 – Project Control
002 – PRINCE2
002 – ISACA
002 – Information and Communication Technology
002 – Incident Resolution
002 – Customer Portfolio
002 – Configuration Item
002 – Compliance Register
001 – TM Forum
001 – Service Model
001 – Service level
001 – Request for Change
001 – Operations Manager
001 – Capacity Manager
001 – Acceptance Test
000 – Test Model
000 – Technical Analyst
000 – Support Request
000 – Status Inquiry
000 – SLA Review
000 – SKMS
000 – Service Transition
000 – Service Review
000 – Service Requirements
000 – Service Portfolio
000 – Service Owner
000 – Service Level Manager
000 – Service Design Package
000 – Service Design
000 – Service Definition
000 – Service Charter
000 – Service Assessment
000 – Security Management Information System
000 – Request for Service
000 – Release Unit
000 – Release Policy
000 – Release Plan
000 – Release Deployment
000 – Release Build
000 – RACI matrix
000 – Purchase Request
000 – Project Coordination
000 – Process Owner
000 – Process Evaluation
000 – Process Area
000 – Process Architecture
000 – Process Architect
000 – Problem Report
000 – Problem Priority
000 – Problem Identification
000 – PDCA
000 – IT Operator
000 – ISO/IEC 27002
000 – ISO/IEC 27001
000 – Ishikawa diagram
000 – Incident Record
000 – Incident Closure
000 – Functional Management
000 – Event Review
000 – Emergency Change
000 – ECAB
000 – Demand Manager
000 – Definitive Media Library
000 – Continual Service Improvement
000 – Configuration Audit
000 – Change Schedule
000 – Change request
000 – Change Record
000 – Change Proposal
000 – Change Owner
000 – Change Evaluation
000 – Change Classification
000 – Capacity Report
000 – Business Relationship Manager
000 – Business case
000 – Budget Request
000 – Best practice
000 – Axelos
000 – Availability Test
000 – Availability Report
000 – Availability Plan
000 – Availability Manager
000 – Access and Identity Management
Patents:
00078000 – Service Request
00062400 – Service level
00059000 – Request for Service
00049600 – Call center
00048000 – Application Development
00032500 – Service Delivery
00032500 – Process Design
00031200 – Risk Management
00027700 – Service Requirements
00027200 – Access Management
00022800 – Service Management System
00022800 – Information Security Manager
00022700 – Application Management
00021400 – Information and Communication Technology
00020700 – Change request
00019600 – Application Developer
00018500 – Application Framework
00017500 – Service Support
00016700 – Test Model
00014200 – Identity management
00013300 – Best practice
00013100 – Service Operation
00011900 – Compliance Register
00011900 – Application Manager
00011100 – Service Model
00010700 – Purchase Request
00010400 – RACI matrix
00010400 – Program management
00010300 – Change Management
00010200 – Request for Change
00009900 – Configuration Manager
00009830 – Help desk
00006900 – Capacity Management
00006400 – Service Definition
00006390 – Release Unit
00006370 – Process Area
00005360 – Status Inquiry
00004960 – Business case
00004690 – IT Operations Manager
00004690 – Facilities Management
00004110 – Process Architect
00004110 – Demand Management
00003910 – Acceptance Test
00003380 – Process Evaluation
00003080 – Configuration Item
00003060 – Availability Management
00002990 – Service Design
00002830 – Compliance Management
00002820 – Service Desk
00002570 – Security Incident
00002420 – Service Design Package
00002420 – Problem Identification
00002420 – Business Service Management
00002340 – Incident Management
00002240 – Release Management
00002220 – Operations Manager
00002190 – Process Architecture
00002120 – Technical Management
00002110 – Risk Monitoring
00001960 – Support Request
00001960 – SLA Review
00001960 – Incident Report
00001930 – CMDB
00001930 – Change Record
00001870 – Service catalog
00001720 – Problem Management
00001450 – Project Control
00001360 – Customer Complaint
00001240 – Test Manager
00001190 – Risk Manager
00001140 – Problem Report
00001020 – Process Owner
00000986 – Strategic Action Plan
00000986 – IT Service Management
00000906 – Supplier Management
00000891 – Emergency Plan
00000839 – Service Strategy
00000824 – Lean manufacturing
00000803 – Service Portfolio
00000771 – Request Fulfillment
00000663 – ITSM
00000646 – Service Owner
00000620 – Process Audit
00000614 – PRINCE2
00000614 – PDCA
00000603 – Functional Management
00000593 – Service Assessment
00000582 – Knowledge Manager
00000580 – Change Evaluation
00000559 – Standard Terms and Conditions
00000559 – Security Management Information System
00000559 – Business Relationship Manager
00000559 – Business Relationship Management
00000559 – Access and Identity Management
00000559 – 5 Whys
00000554 – Change Manager
00000521 – Security Review
00000513 – Change Schedule
00000490 – Agile software development
00000488 – Customer Portfolio
00000485 – Compliance Manager
00000478 – Business impact analysis
00000445 – Event Review
00000430 – Service Review
00000428 – Availability Manager
00000413 – Compliance Review
00000406 – Configuration Audit
00000404 – Availability Report
00000396 – Incident Record
00000387 – Release Build
00000369 – Incident Resolution
00000368 – Capacity Plan
00000363 – Risk Management Policy
00000359 – Availability Test
00000339 – Change Classification
00000316 – Capacity Manager
00000314 – Service Catalogue
00000295 – Axelos
00000278 – Service Transition
00000277 – Change Owner
00000271 – Release Plan
00000263 – Service Charter
00000263 – Capacity Report
00000259 – Release Planning
00000245 – COBIT
00000227 – Incident Manager
00000217 – IT Operator
00000214 – Service Level Manager
00000207 – IT Operations Management
00000201 – Change Proposal
00000199 – Budget Request
00000192 – Release Policy
00000163 – Project Coordination
00000156 – Emergency Change
00000139 – Release Deployment
00000139 – Demand Manager
00000127 – TM Forum
00000126 – Problem Priority
00000116 – Project Charter
00000116 – Fishbone diagram
00000104 – Corrective and preventive action
00000096 – Technical Analyst
00000090 – Risk Register
00000076 – SKMS
00000073 – ISO/IEC 27002
00000073 – ISO/IEC 27001
00000073 – ISACA
00000072 – Supplier Manager
00000067 – Service Portfolio Management
00000067 – Continual Service Improvement
00000057 – ECAB
00000041 – Availability Plan
00000030 – Ishikawa diagram
00000028 – Incident Closure
00000000 – Definitive Media Library
00000000 – Change Management Policy
Books in print:
00084800 – Best practice
00058031 – IT Operator
00046200 – Risk Management
00023874 – Information and Communication Technology
00020522 – IT Operations Management
00018275 – Service Delivery
00016710 – Change Management
00011894 – Call center
00011768 – Application Development
00011453 – Business case
00009799 – IT Service Management
00009770 – Service level
00008666 – 5 Whys
00007912 – Customer Complaint
00006768 – Service Support
00005835 – Help desk
00005310 – Facilities Management
00004020 – Operations Manager
00003676 – Incident Report
00003314 – Emergency Plan
00003286 – Change request
00002996 – Service Operation
00002918 – Demand Management
00002904 – Incident Management
00002801 – Budget Request
00002628 – Application Developer
00002428 – Service Model
00002413 – Lean manufacturing
00002259 – Service Request
00002042 – Acceptance Test
00002008 – Identity management
00001996 – Agile software development
00001901 – Process Evaluation
00001813 – Service Design
00001763 – Service Desk
00001741 – Service Review
00001728 – Problem Identification
00001699 – Request for Change
00001646 – Problem Management
00001636 – PRINCE2
00001613 – Application Management
00001579 – Process Owner
00001516 – Security Incident
00001478 – Service Requirements
00001465 – Service Strategy
00001400 – Security Review
00001386 – Application Framework
00001367 – Fishbone diagram
00001350 – Test Model
00001320 – Access Management
00001251 – Configuration Item
00001203 – Configuration Manager
00001160 – Capacity Management
00001156 – Project Charter
00001133 – Risk Register
00000968 – Business impact analysis
00000940 – Problem Report
00000912 – Technical Analyst
00000901 – Request for Service
00000859 – Process Area
00000853 – Risk Management Policy
00000826 – Change Manager
00000823 – ISO/IEC 27001
00000725 – Supplier Management
00000716 – Change Schedule
00000713 – Compliance Review
00000712 – COBIT
00000686 – Process Architecture
00000656 – Compliance Management
00000654 – Service Definition
00000631 – Release Management
00000606 – Ishikawa diagram
00000604 – ITSM
00000578 – PDCA
00000577 – Service catalog
00000556 – Continual Service Improvement
00000540 – Service Portfolio
00000523 – Standard Terms and Conditions
00000512 – Availability Management
00000492 – Support Request
00000448 – Release Plan
00000447 – Change Proposal
00000428 – Service Transition
00000419 – Change Record
00000398 – Knowledge Manager
00000391 – Test Manager
00000382 – Purchase Request
00000379 – ISACA
00000360 – Capacity Plan
00000345 – Risk Monitoring
00000345 – Functional Management
00000339 – Application Manager
00000337 – Release Planning
00000335 – Information Security Manager
00000328 – CMDB
00000322 – Release Build
00000320 – Change Management Policy
00000313 – Process Audit
00000303 – Incident Record
00000302 – Business Relationship Management
00000300 – Change Owner
00000289 – Event Review
00000280 – Service Management System
00000262 – Release Deployment
00000241 – Configuration Audit
00000240 – Service Owner
00000240 – Service Catalogue
00000238 – Change Evaluation
00000236 – Release Policy
00000236 – Emergency Change
00000221 – Service Portfolio Management
00000221 – Project Coordination
00000212 – Customer Portfolio
00000207 – Problem Priority
00000193 – Change Classification
00000193 – Axelos
00000188 – Release Unit
00000184 – Compliance Manager
00000182 – RACI matrix
00000151 – SKMS
00000144 – Incident Manager
00000140 – Availability Report
00000132 – Service Level Manager
00000130 – Incident Resolution
00000126 – Definitive Media Library
00000120 – Business Relationship Manager
00000090 – Capacity Report
00000086 – Demand Manager
00000086 – Availability Plan
00000074 – TM Forum
00000070 – Service Charter
00000070 – Security Management Information System
00000068 – Capacity Manager
00000063 – Status Inquiry
00000062 – Supplier Manager
00000061 – Process Architect
00000061 – Incident Closure
00000060 – Service Design Package
00000047 – Availability Test
00000043 – Access and Identity Management
00000025 – SLA Review
00000000 – Technical Management
00000000 – Strategic Action Plan
00000000 – Service Assessment
00000000 – Risk Manager
00000000 – Request Fulfillment
00000000 – Project Control
00000000 – Program management
00000000 – Process Design
00000000 – IT Operations Manager
00000000 – ISO/IEC 27002
00000000 – ECAB
00000000 – Corrective and preventive action
00000000 – Compliance Register
00000000 – Business Service Management
00000000 – Availability Manager
Youtube content:
02320000 – Risk Management
00389000 – Call center
00169000 – Best practice
00145000 – Business case
00145000 – Application Development
00137000 – Change Management
00109000 – Help desk
00084400 – Service Delivery
00075200 – Lean manufacturing
00060700 – Service Review
00056700 – Operations Manager
00056400 – Test Model
00043700 – Event Review
00043300 – Service Desk
00029500 – ITSM
00027700 – Service Design
00024500 – Configuration Manager
00024000 – Security Review
00023700 – Facilities Management
00023600 – PDCA
00021700 – Incident Management
00020600 – Program management
00019800 – Identity management
00019100 – PRINCE2
00017100 – Technical Analyst
00015300 – IT Service Management
00015300 – Access Management
00015200 – Project Control
00014700 – COBIT
00014200 – Application Developer
00013200 – Incident Report
00013200 – Agile software development
00012900 – Service Support
00012800 – Service level
00012600 – Information and Communication Technology
00012300 – Service Model
00012100 – Risk Manager
00012100 – Process Design
00011200 – Release Build
00009680 – Emergency Plan
00009420 – ECAB
00008870 – Application Framework
00008830 – Customer Complaint
00008700 – Service Request
00008370 – Application Management
00007850 – ISACA
00007730 – Release Management
00007620 – Service catalog
00007580 – Acceptance Test
00007480 – CMDB
00007340 – SKMS
00007330 – Test Manager
00007330 – Service Strategy
00007200 – Budget Request
00007120 – Compliance Management
00006980 – Service Operation
00006370 – Project Charter
00006140 – Application Manager
00005780 – 5 Whys
00005690 – Security Incident
00005190 – Capacity Management
00005170 – Fishbone diagram
00004660 – TM Forum
00004610 – Change request
00004480 – Problem Management
00004310 – Business Service Management
00004270 – Demand Management
00003860 – Service Portfolio
00003790 – Compliance Manager
00003540 – Support Request
00003500 – Problem Report
00003350 – Supplier Management
00003050 – Release Plan
00002920 – Risk Register
00002890 – Change Manager
00002720 – Service Transition
00002540 – Ishikawa diagram
00002490 – Service Management System
00002470 – Release Planning
00002420 – Change Proposal
00002410 – IT Operations Management
00002400 – ISO/IEC 27001
00002230 – Service Requirements
00002020 – Business impact analysis
00001930 – Problem Identification
00001900 – Axelos
00001810 – Service Owner
00001780 – Technical Management
00001670 – Change Record
00001590 – Availability Management
00001570 – Process Evaluation
00001550 – Standard Terms and Conditions
00001530 – Purchase Request
00001530 – Information Security Manager
00001520 – Continual Service Improvement
00001510 – Business Relationship Management
00001480 – Project Coordination
00001430 – Service Charter
00001260 – Service Definition
00001120 – Process Architecture
00000950 – Incident Manager
00000915 – Service Catalogue
00000912 – Release Policy
00000873 – Request Fulfillment
00000863 – Change Schedule
00000862 – Compliance Review
00000857 – Risk Monitoring
00000850 – Release Unit
00000845 – Change Owner
00000801 – Process Audit
00000727 – Request for Change
00000639 – Process Area
00000635 – Strategic Action Plan
00000585 – Service Portfolio Management
00000559 – Knowledge Manager
00000546 – Business Relationship Manager
00000535 – Availability Manager
00000522 – Customer Portfolio
00000510 – Corrective and preventive action
00000480 – Configuration Item
00000442 – Process Owner
00000440 – Service Assessment
00000381 – Request for Service
00000352 – Functional Management
00000337 – Risk Management Policy
00000322 – IT Operations Manager
00000316 – IT Operator
00000313 – Availability Report
00000283 – Status Inquiry
00000283 – Incident Resolution
00000276 – ISO/IEC 27002
00000268 – RACI matrix
00000263 – Incident Record
00000262 – Demand Manager
00000235 – Availability Test
00000227 – Capacity Plan
00000198 – Emergency Change
00000150 – Supplier Manager
00000139 – Process Architect
00000131 – Configuration Audit
00000127 – Change Evaluation
00000120 – Release Deployment
00000119 – SLA Review
00000107 – Capacity Manager
00000092 – Capacity Report
00000077 – Service Level Manager
00000056 – Service Design Package
00000053 – Compliance Register
00000035 – Availability Plan
00000026 – Definitive Media Library
00000018 – Problem Priority
00000017 – Access and Identity Management
00000012 – Change Management Policy
00000011 – Change Classification
00000003 – Security Management Information System
00000002 – Incident Closure
Start with Compliance Manager, Information Security Manager, Operations Manager, and make the above top Predictive Analytics results happen:
Access all the ITIL Prescriptive Analytics Compliance Manager, Information Security Manager, Operations Manager, blueprints, presentations and templates and much more in The Art of Service LAB theartofservice.co/lab. Sign up for 7 days free today.